AWS-Vault Tutorial: Securing Your Secrets on AWS
Securing access to AWS accounts is a top priority for organizations in cloud computing. As someone deeply involved with cloud infrastructure, I understand the complexities of handling multiple AWS accounts. That’s where a tool like aws-vault becomes indispensable. It allows me to efficiently manage and switch between accounts without the hassle of keeping track of various access keys and credentials.
My mission is straightforward: to simplify accessing AWS accounts while maintaining strict security protocols. This will boost productivity and fortify the organization’s security posture. Using aws-vault is a game-changer; it keeps sensitive information from my shell history and off my local development machine, replacing many passwords with a single unlock method. Whether I’m deploying applications to an EC2 instance or managing infrastructure with Terraform, aws-vault supports a seamless transition across tasks with fortified security.
Understanding AWS-vault
AWS-vault is a tool I rely on for managing my AWS credentials with the highest security. It lets me create discrete profiles for each AWS account, making it straightforward to switch contexts without confusion. Whenever I use AWS CLI, I designate the desired profile, alleviating the need to recall each account’s details.
The process starts when I initialize a new profile using the aws-vault add command. This step secures my AWS access and secret keys by encrypting and tucking them away securely. When it’s time to switch profiles, I execute aws-vault exec and input the relevant password to gain access to another account.
Most importantly, AWS-vault maximizes security through transient credentials obtained from Amazon’s STS service. These are produced through GetSessionToken or AssumeRole API calls and have a limited lifespan. Since these credentials are temporary, the danger of being compromised is significantly lessened. This feature is particularly valuable in maintaining the integrity of my AWS access.
Managing Credentials for AWS Services
Here’s a quick getting started guide.
Setting Up the Tool
For those already using zsh and oh-my-zsh, installing the necessary tool to handle AWS credentials securely is straightforward. On macOS, a simple command gets the job done:
brew cask install aws-vaultHere’s the complete list of installation steps for the most available platforms.
Selecting a Storage Solution
The tool provides flexibility with multiple storage options for your credentials:
- macOS Keychain
- Windows Credential Manager
- Gnome Keyring
- KWallet
- Pass
- Encrypted file
My personal preference leans toward the encrypted file for the ease of backing up to an S3 bucket. Should you choose this method, add this line to your ~/.zshrc file:
export AWS_VAULT_BACKEND="file"Transferring Existing Credentials
Access the ~/.aws/credentials file to start transferring existing profile information into the tool. Here’s how to add profiles:
cat ~/.aws/credentials
aws-vault add profile_1
aws-vault add profile_2To avoid frequent password prompts, set the AWS_VAULT_FILE_PASSPHRASE environment variable. This is achievable via two methods:
Less secure: Add to your shell configuration file (~/.zshrc or ~/.bashrc):
export AWS_VAULT_FILE_PASSPHRASE="my_strong_password"More secure: Store your password using AWS Systems Manager Parameter Store‘s SecureString:
aws ssm put-parameter \
--name '/laptop/aws-vault/password' \
--description 'aws-vault password on my laptop' \
--value 'my_super_secret_password' \
--type SecureString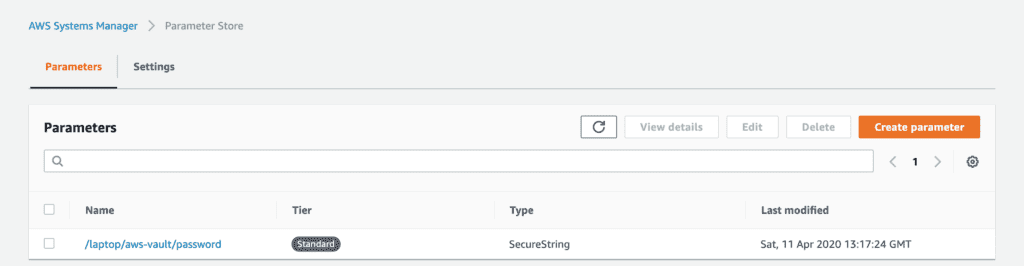
I suggest creating a script for frequent use that retrieves your password securely:
mkdir -p $HOME/bin
cat > $HOME/bin/call-aws-vault.sh <<- EOF
#!/usr/bin/env bash
export PROFILE=$1
export AWS_VAULT_FILE_PASSPHRASE=$(aws ssm get-parameters --profile default --names '/laptop/aws-vault/password' --with-decryption --query 'Parameters[0].Value' --output text)
aws-vault exec -j $PROFILE
EOF
chmod +x $HOME/bin/call-aws-vault.shIncorporate this within the ~/.aws/config:
[profile my_new_profile]
credential_process = ~/bin/call-aws-vault.sh my_new_profileAfter a successful test run, you can phase out the original ~/.aws/credentials file.
Navigating Between Profiles
To review all configured AWS profiles, use:
aws-vault listChanging environments is also a quick command away, granting the desired access for 8 hours:
aws-vault exec --duration 8h default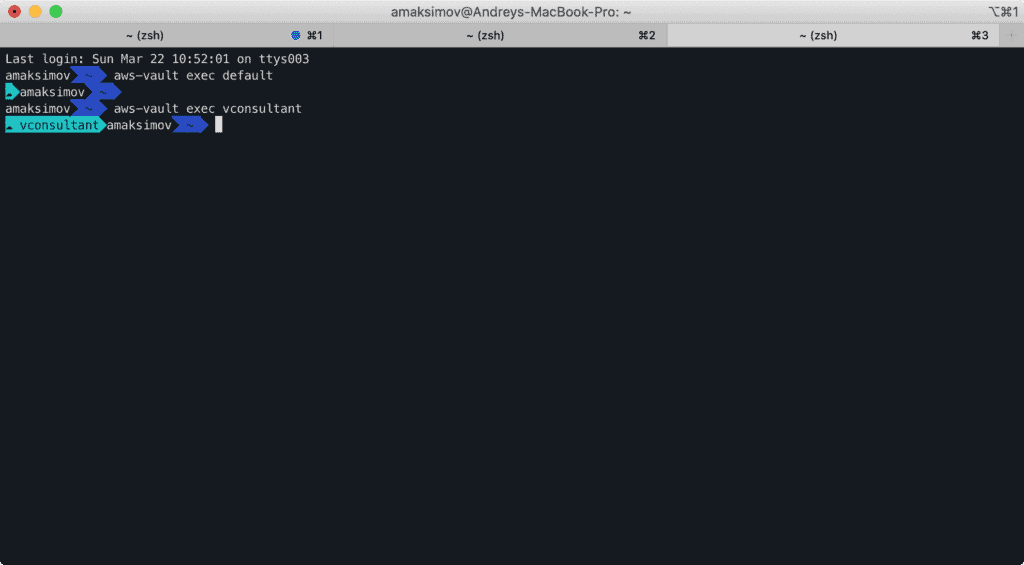
This enables the effective use of various AWS CLI tools, Terraform, or AWS CDK across different sessions.
Hierarchical Permissions Management
Structuring Access Across Multiple Accounts
Managing access to Amazon Web Services involves setting up a centralized structure where all Identity and Access Management (IAM) users are housed within a single account. This primary account allows access to additional accounts by adopting IAM roles. This method uses the Amazon Security Token Service AssumeRole function to facilitate cross-account permissions.
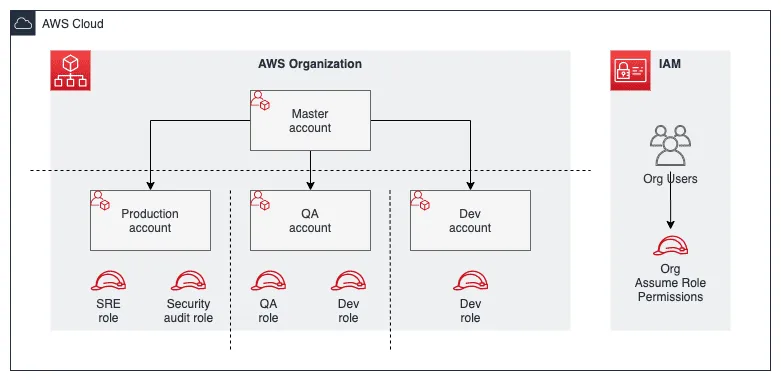
Consider a standard AWS organization setup:
- A centralized IAM user repository exists.
- These users assume roles in other accounts to perform actions without needing individual IAM users in each account.
Initial Configuration of the Primary Profile
In the primary profile setup, the credentials are defined as follows:
- Region set to us-east-1
To integrate aws-vault for credentials management:
[profile default]
region = us-east-1
credential_process = /usr/local/bin/aws-vault exec -j defaultAfterward, if permissions are allocated for your user or role to assume an AWS role in another account, you can configure profiles accordingly:
[profile account_1_role_admin]
region = us-east-1
role_arn = arn:aws:iam::account-id:role/admin
source_profile = default
[profile account_2_role_qa]
region = us-east-1
role_arn = arn:aws:iam::account-id:role/qa
source_profile = defaultsource_profile configuration option will tell AWS CLI which account to use to grab a role for any given profile.
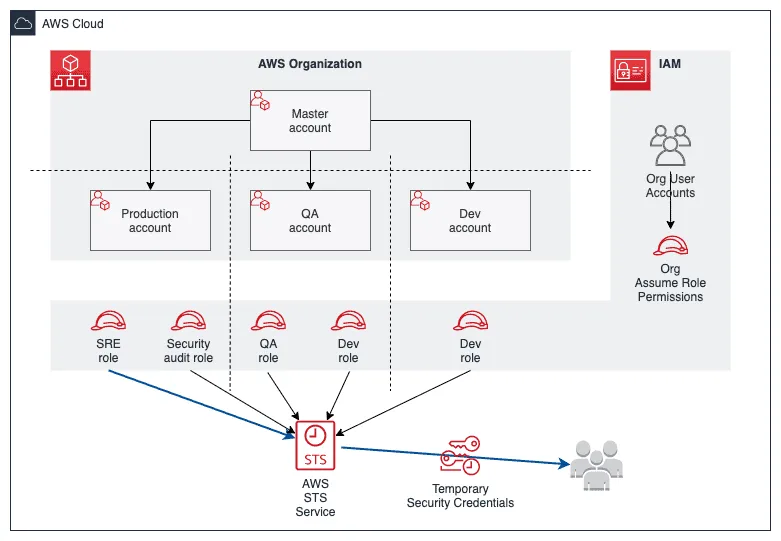
Verification Procedures
To ensure role assumption is functioning correctly, execute the following command for the default profile:
aws sts get-caller-identifyThe expected response should resemble:
{
"UserId": "AIDDRCTFVGBHNJMGF3WI7R",
"Account": "01234567890",
"Arn": "arn:aws:iam::01234567890:user/admin"
}For testing other profiles, replace ‘default’ with the specific profile name as such:
aws sts get-caller-identity --profile account_1_role_adminThis should produce an output that confirms the role’s assumption:
{
"UserId": "AROALKJHGFGDFV3IR2VSI:botocore-session-1584897134",
"Account": "012345678901",
"Arn": "arn:aws:sts::012345678901:assumed-role/admin/botocore-session-1584897134"
}Verification ensures that IAM policies and roles are correctly assumed across your AWS organization, providing a secure and streamlined access management system.
Assuming the AWS Account Role
To switch roles within AWS, I utilize aws-vault with the following steps:
- List Available Profiles
aws-vault ls
- Initiate Session with a Role
- Command:
aws-vault exec --duration 8h default - Duration: This session remains active for 8 hours.
- Session Details: Ensures access using temporary credentials provided by
sts:AssumeRole.
- Command:
Enhanced AWS Identity Management
AWS SSO simplifies the process of accessing various AWS applications by centralizing identity management. By integrating aws-vault SSO support with AWS SSO CLI v2, I can facilitate quick and secure access to AWS environments. The secure vault stores AWS credentials, leveraging AWS SSO for environment access when necessary.
- Streamlined Access: Single credentials for multiple services.
- Secure Storage: Credentials safely stored in vault.
- AWS SSO Integration: Smooth interfacing with AWS environments.
Passwordless AWS Web Console Login
Using aws-vault, I seamlessly perform safe sign-ins to the AWS console. This tool leverages my MacOS Keychain or Windows Credential Manager to store tokens securely, removing the need for a passphrase. When I need to authenticate, aws-vault utilizes these tokens to grant access, eliminating manual MFA or IAM user authentication steps. Here’s a quick command for an 8-hour session:
- Open terminal
- Input:
aws-vault login --duration 8h default
Securely Ending the AWS Shell Session
To safeguard my account, I terminate my AWS shell session with the Ctrl+D shortcut. This prevents unauthorized access.
Overview
By integrating zsh, aws-vault, and the AWS sts:AssumeRole service, I enhance security and streamline the management of various AWS account credentials.
