Amazon Inspector is an automated security assessment service in the AWS cloud because it provides automated security assessments of applications and resources inside an Amazon Web Services (AWS) environment. It helps identify potential security weaknesses, such as insecure network configurations and vulnerable software components across EC2 instances, Lambda functions, and container images in your AWS account. Additionally, the service can continuously monitor and protect against threats (including unintended network exposure) by providing proactive notifications of potential vulnerabilities or misconfiguration.
This article contains the most important information about the AWS Inspector service. Let’s get started.
What is Amazon Inspector?
Amazon Inspector is a security assessment service that helps improve the security testing and compliance of applications deployed on Amazon Web Services (AWS). It automates identifying security software vulnerabilities and deviations from best practices in application and infrastructure deployments across AWS workloads, providing customers with actionable recommendations for remediation. AWS Inspector can assess EC2 instances, Docker images stored in the ECR registry, Lambda functions (including images), and perform network reachability tests to identify open ports and potential security gaps.
Once activated, Amazon Inspector continuously scans AWS workloads for potential issues providing detailed assessment reports in the AWS Management Console with security findings prioritized:
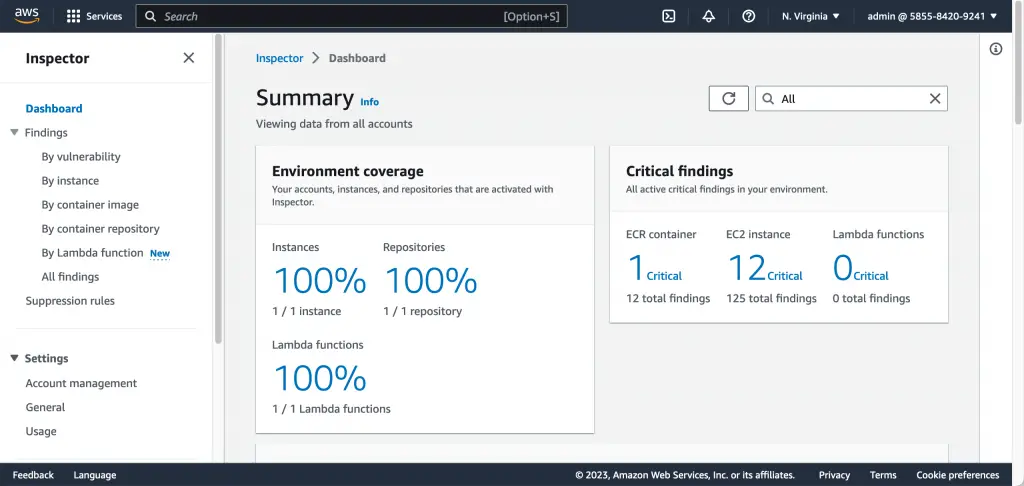
For automated remediation actions or notifications, you need to use Amazon EventBridge notifications, e.g., Creating custom responses to Amazon Inspector findings with Amazon EventBridge.
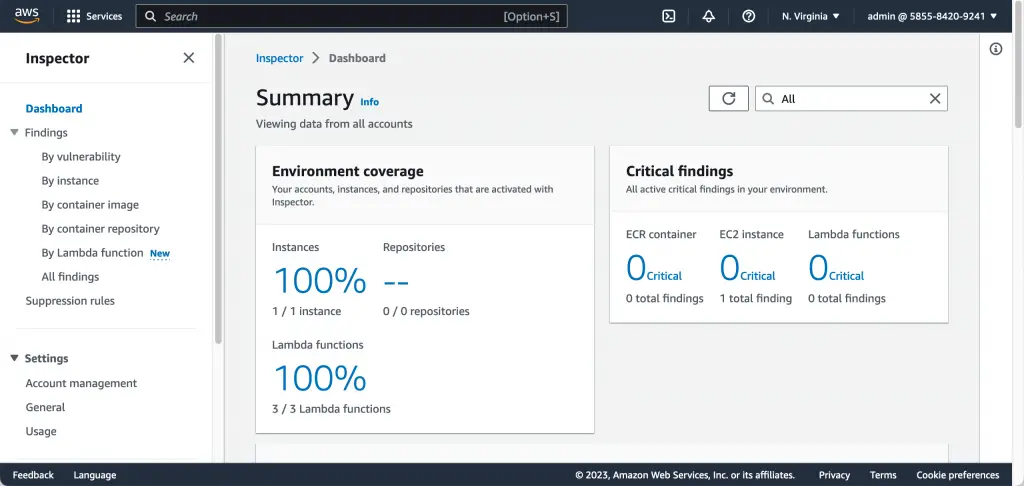
Once security vulnerabilities are identified, you can use AWS Systems Manager Patch Manager and AWS Systems Manager Maintainance Windows to configure automated EC2 instances patching and OS updates. It takes several minutes for AWS Inspector to identify that issues have been remediated:
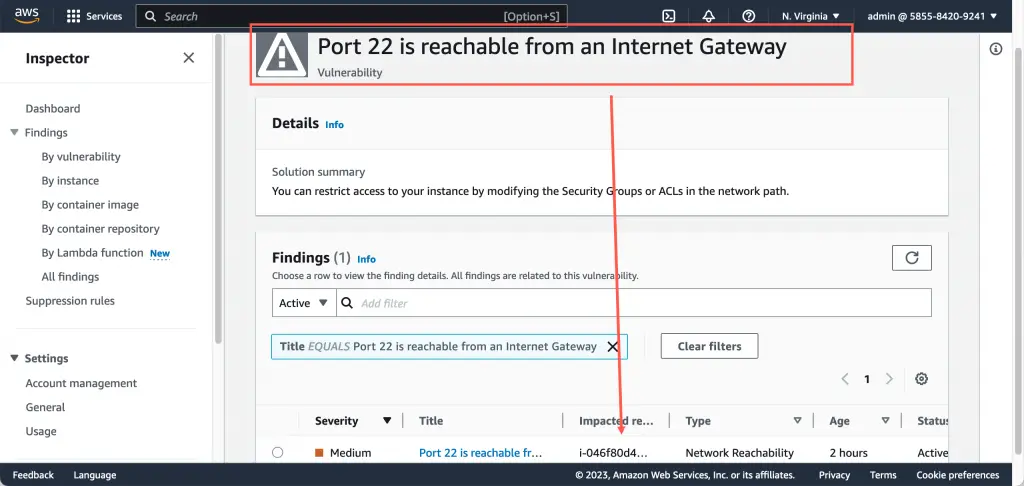
Pay attention that Amazon Inspector Dashboard shows only critical vulnerabilities. To see medium and low vulnerabilities, for example, network accessibility findings, go to the “Findings” section of the menu:
Features
AWS Inspector features include:
- Vulnerability assessments: AWS Inspector assesses the security of Amazon EC2 instances, containers, and AWS resources and identifies vulnerabilities that attackers could exploit.
- Compliance checks: AWS Inspector checks applications against industry standards and best practices, such as SOC, PCI, FedRAMP, HIPAA, and others.
- Automated assessments: AWS Inspector automates the assessment process, reducing the time and effort required to identify and remediate security vulnerabilities.
- Integration with other AWS security tools: AWS Inspector integrates with other AWS security and monitoring services, such as Amazon GuardDuty, AWS Security Hub, and Amazon CloudWatch, to provide a comprehensive security solution.
- Reporting and notifications: AWS Inspector provides detailed reports and notifications, making it easy to track progress and take action to remediate vulnerabilities.
- Scalability: AWS Inspector can be used to assess large-scale deployments, making it an ideal solution for customers with many resources to assess.
Pricing
AWS Inspector pricing consists of the following components:
- The average number of Amazon EC2 instances scanned per month
- Number of container images scanned initially on-push to Amazon ECR per month
- Number of automated rescans for container images in Amazon ECR configured for continuous scanning per month
- The average number of AWS Lambda functions scanned per month
Security Best Practices
Here are some best practices for using Amazon Inspector we recommend implementing in your daily security operations:
- Regular Assessment: Continuously monitor the security of your AWS resources.
- Prioritize Recommendations: Prioritize the recommendations provided by AWS Inspector based on the severity of the issue and the potential impact on your environment. Act immediately to remediate them.
- Follow AWS Security Best Practices: Follow the security best practices recommended by AWS Well-Architected Framework when setting up and configuring your AWS resources.
- Monitor Assessment Results: Regularly monitor the results of the assessments to ensure that vulnerabilities are being remediated on time.
- Secure Your Assessment Environment: Ensure that the environment used to run AWS Inspector assessments is secure and protected from unauthorized access.
- Centralize Reporting: Centralize the reporting of the results of the assessments to ensure that all stakeholders have access to the information they need to improve security and compliance.
- Automate Notifications and Remediation Steps: Automate notifications when certain conditions are met. You can also automate remediation steps to address threats quickly and efficiently.
- Train Personnel: Train personnel on using AWS Inspector to ensure that they can use the service effectively and understand the security implications of their actions. Security department personnel must also have clear instructions on acting for each security incident.
By following these best practices, you can effectively use AWS Inspector to continuously monitor and improve your AWS deployments’ security.
