AWS CloudTrail is a critical service because it provides visibility into user activity and resource changes within an AWS account. It logs all API calls to create a complete audit trail, which can be used for security, operational troubleshooting, and compliance auditing. CloudTrail also helps track when specific users, roles, or services change resources in an AWS account so that any unauthorized actions can be quickly identified and remediated.
This article provides the most important information about the AWS CloudTrail service. Let’s get started.
What is an AWS CloudTrail?
AWS CloudTrail is a service that helps track user activity and API usage (management events) in an AWS environment. It delivers security logs with the details of the API calls to AWS CloudWatch or a centralized S3 bucket. It provides visibility into user and AWS services activity, such as user logins and API calls, by recording all actions taken on the AWS Management Console and interaction with APIs through Amazon Web Services SDK or command line tools. By analyzing CloudTrail events, you can review users’ and services’ activity and gain insights into operational and security-related issues.
You can access AWS CloudTrail and manage it through:
- AWS Management Console
- Infrastructure as Code (IaC) tools:
- SDKs
- AWS CLI
Pay attention that ALL AWS services are integrated with AWS CloudTrail. Whenever you’re using AWS through AWS Management Console, any tool or service that interacts with AWS, these interactions are going through AWS APIs. AWS CloudTrail tracks and stores the history of all API calls for future analysis.

You can review CloudTrail Event history in the AWS Management Console:
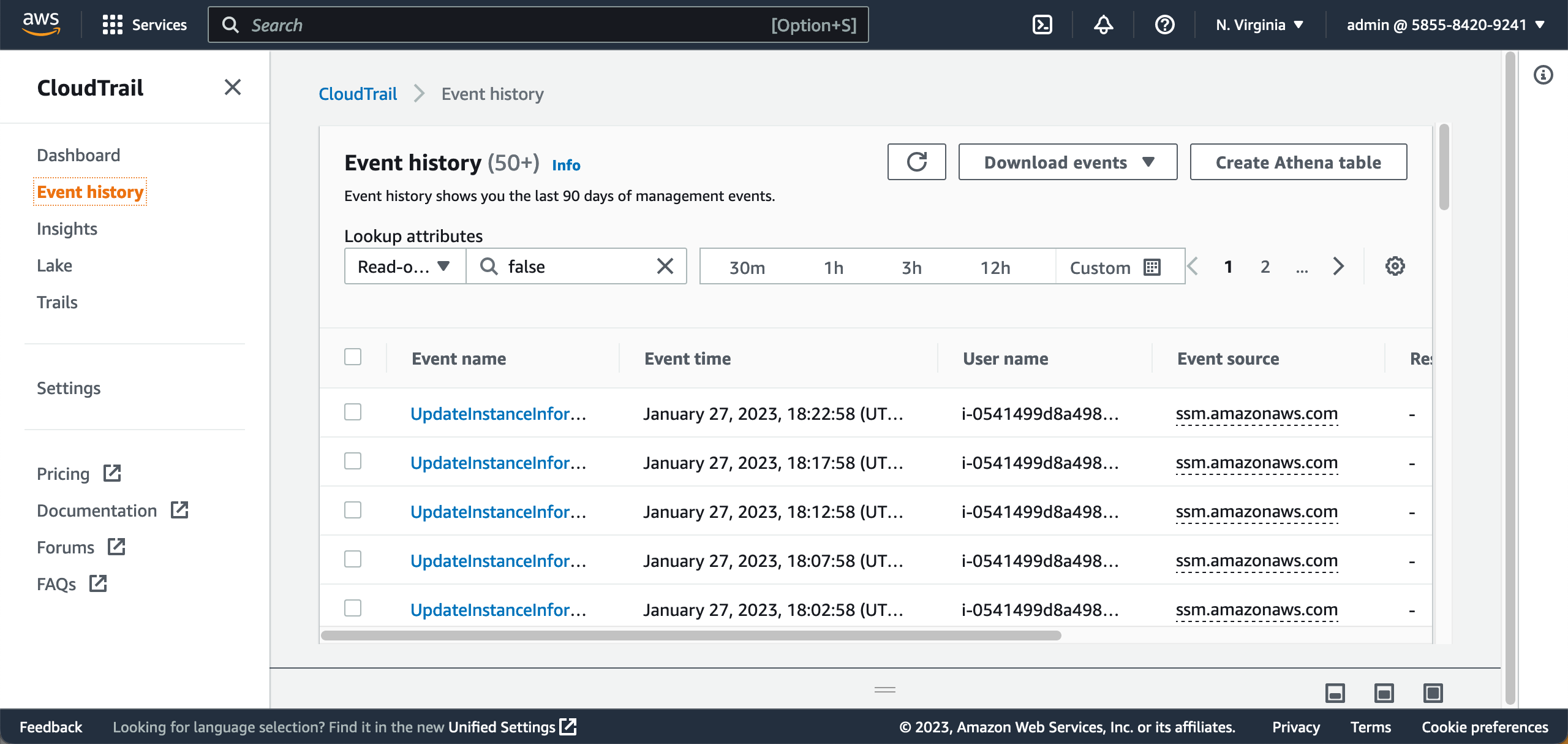
The information available in AWS CloudTrail Logs:
- Event time – when the event happened
- Event name – what happened
- User name – who performed an API call
- Event source – which service performed an API call
- AWS Access Key – associated with the API call
- Source IP address
- AWS region
- Read-only – tells if the operation was read-only or the API call made some changes
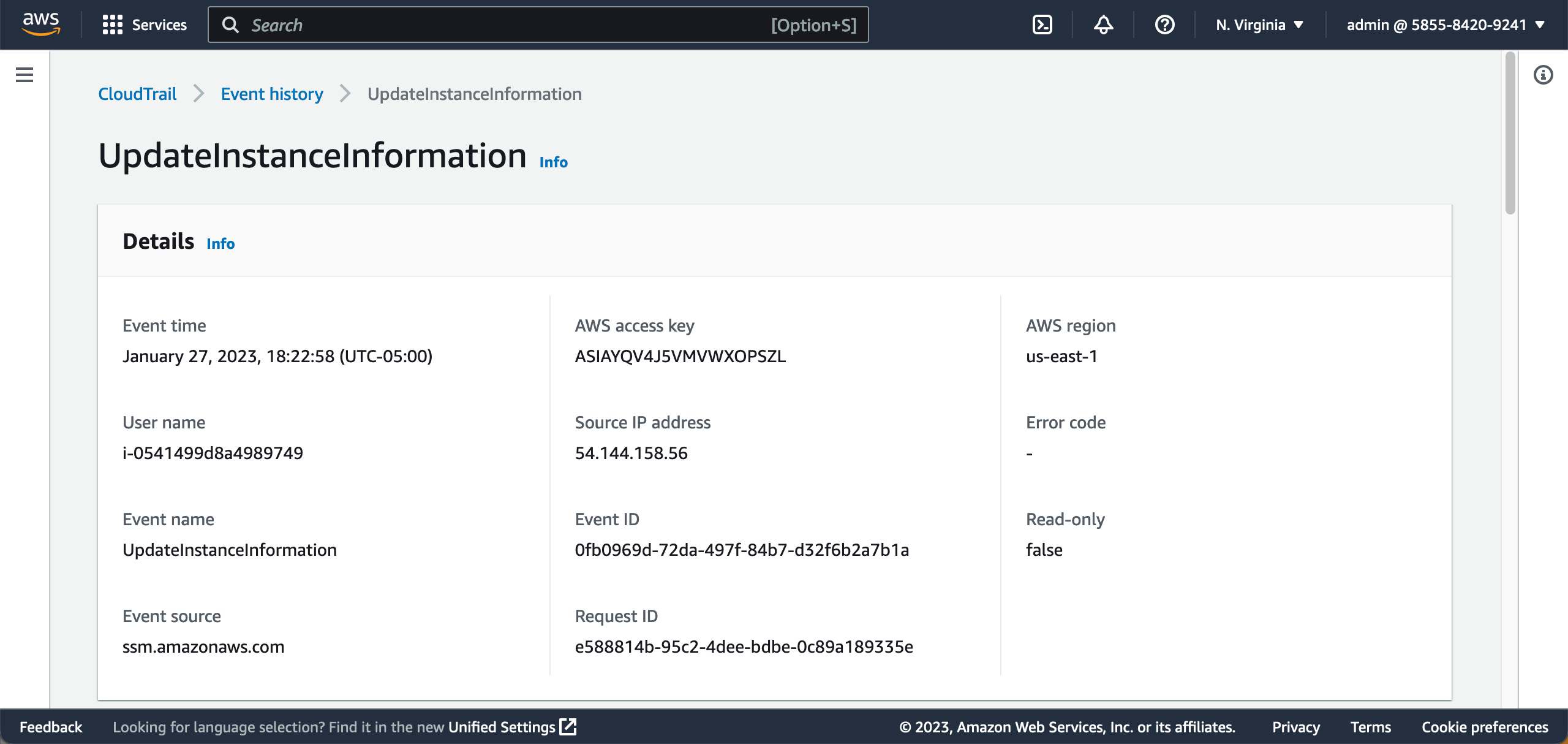
Check some complete examples of log events in the CloudTrail log event reference guide.
Additionally, AWS CloutTrail Insights allows you to pay attention to the unusual events in your AWS account API activity:
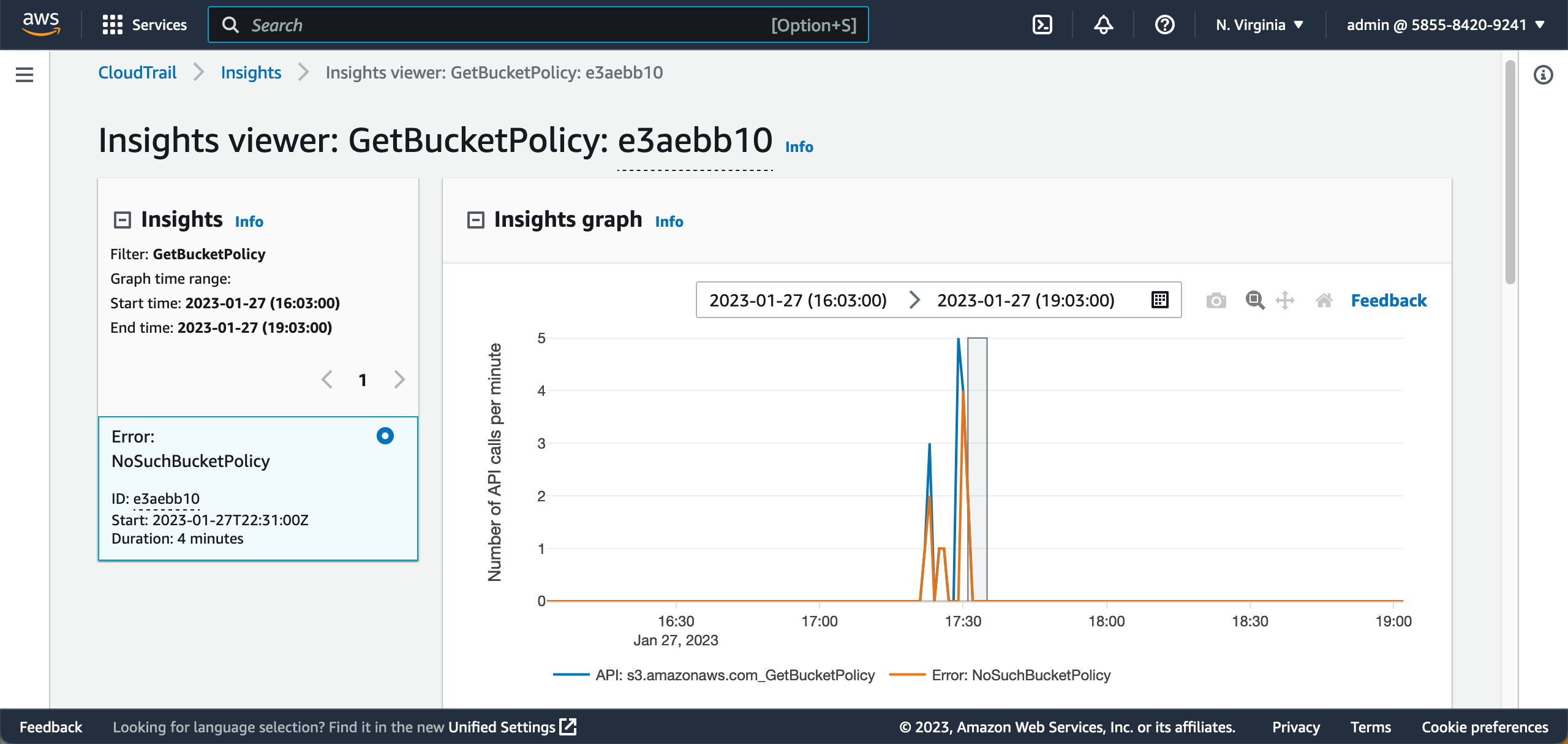
CloudTrail Insights events can be captured by the EventBridge and processed by AWS Lambda.
AWS CloudTrail is a regional AWS service, and you MUST configure AWS CloudTrail in every AWS account and region you’re willing to use in the cloud.
What Is The Purpose Of CloudTrail?
By capturing CloudTrail Logs and events, Cloud Engineers and Security Engineers can:
- Store event AWS event history and management events in a central location (S3 bucket)
- Do security log files integrity validation
- Do security incidents analysis of AWS account management events
- Resource change tracking (use with AWS Config for better visibility and faster response)
- Compliance auditing (use with AWS Config for better visibility and faster response)
AWS CloudTrail Important Integrations
AWS CloudTrail delivers its logs to an Amazon S3 bucket or optionally to the Amazon CloudWatch Logs, and you can use the following AWS services to work with this data:
- Amazon CloudWatch Events and CloudWatch Alarms – allows triggering any automation in response to the critical events
- Amazon EventBridge – allows you to filter events and required API calls and react on them using AWS Lambda, for example
- AWS Lambda – allows reacting to specific API calls filtered by EventBridge rules, e.g., sending Slack notifications, automatically blocking user/service activity, etc.
- Amazon S3 – provides centralized storage for CloudTrail events and allows analyzing management and data events using Athena, QuickSight, or any other solution.
- Amazon SNS – send SNS notifications
- Amazon Athena – allows Query log information from CloudTrail logs using SQL
- Amazon QuickSight – Build SecurityOps dashboards displaying the account activity incidents
Additionally, it is highly recommended to enable CloudTrail log file integrity validation on the CloudTrail side. And enable S3 Versioning and configure MFA delete for the CloudTrails Logs S3 bucket to prevent the logs from being modified or accidentally deleted.
CloudTrail Logs Consolidation
You can consolidate all CloudTrail events across your entire AWS infrastructure using AWS Organization in a central location – a central S3 bucket in, for example, a Security AWS account.

Free AWS workshops
We recommend you check the following AWS CloudTrail Workshops to get hands-on experience using the service:
